影響全球近1900萬IP地址的大型殭屍網絡「911 S5」被搗破
「911 S5」殭屍網絡影響全球近1900萬個IP地址,對網絡安全構成重大威脅。2024年5月,美國FBI連同多國執法機構聯合行動,成功搗破「911 S5」殭屍網絡 [1]。雖然「911 S5」殭屍網絡已被搗破,但其影響力依然不容忽視。本文將探討其運作方式及移除方法。

什麼是「911 S5」?
「911 S5」是一個大規模的殭屍網絡,主要提供網絡代理服務。其提供的網絡代理服務會使用來自受感染裝置的 IP 地址。網絡犯罪分子購買網絡代理服務後,可使其網絡活動看起來像是來自受感染裝置的網絡,從而隱藏自己的網絡足跡。網絡犯罪分子會利用這些網絡代理服務,通過受感染的裝置重新路由其網絡流量,隱藏其真實的原始 IP 位址和位置,並匿名實施各種犯罪行為 [1]。
「911 S5」透過分發內建惡意程式的 VPN 應用程式針對Windows系統散播。這些 VPN 應用程式通常被植入於盜版遊戲或軟件中,吸引受害者下載。當受害者下載並安裝這些軟件後,VPN應用程式和惡意軟件會在未經同意的情況下悄然安裝到受害者裝置上,將受害者裝置變成「911 S5」殭屍網絡的一部分。與 「911 S5」服務連接的 VPN 應用程式包括:MaskVPN、DewVPN、PaladinVPN、ProxyGate、ShieldVPN 和 ShineVPN [1]。
「911 S5」殭屍網絡的興衰
「911 S5」殭屍網絡大約在 2014 年出現,隨著時間推移,逐漸發展成影響超過 1900 萬個 IP 地址的殭屍網絡。「911 S5」殭屍網絡通過向網絡犯罪分子提供網絡代理服務來產生可觀的收入,同時促成了大量惡意活動,例如金融犯罪、網絡攻擊和數據盜竊等 [1][2][3]。
2022 年 7 月,「911 S5」殭屍網絡因出現重大安全漏洞,最終迫使其管理員將其下線 [4]。 然而,到2023 年 10 月「911 S5」殭屍網絡更名為「CloudRouter」捲土重來。但在多國執法機構努力下最終取得重大突破,成功於 2024 年 5 月逮捕了該殭屍網絡的管理員,「911 S5」殭屍網絡最終被搗破 [1]。
如何移除「911 S5」
即使「911 S5」殭屍網絡已經被搗破,受感染裝置仍存在網絡安全風險,因此需要立即移除與「911 S5」相關的 VPN 應用程式。以下是美國 FBI 提供的檢查和移除「911 S5」殭屍網絡的步驟 [1] (只提供英文版本):
- Press Control+Alt+Delete on the keyboard and select the “Task Manager” option or right-click on the Start menu (Windows icon) and select the "Task Manager" option.

- Task Manager should now be running. Under the "Process" tab, look for the following:
- MaskVPN (mask_svc.exe)
- DewVPN (dew_svc.exe)
- PaladinVPN (pldsvc.exe)
- ProxyGate (proxygate.exe, cloud.exe)
- ShieldVPN (shieldsvc.exe)
- ShineVPN (shsvc.exe)
Example of running processes for ShieldVPN and ShieldVPN Svc:
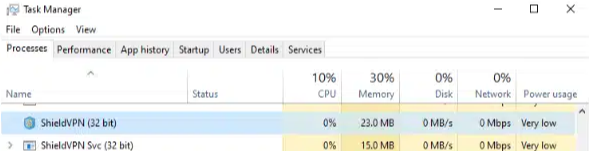
If Task Manager doesn't detect any of these services, verify that by searching the Start menu for any traces of software labeled as "MaskVPN", "DewVPN", "ShieldVPN", "PaladinVPN", "ProxyGate" or "ShineVPN".
- Click on the "Start" (Windows Icon) button typically found in the lower lefthand corner of the screen. Then, search for the following terms, which are the identified names of the malicious software applications:
- MaskVPN
- DewVPN
- ShieldVPN
- PaladinVPN
- ShineVPN
- ProxyGate
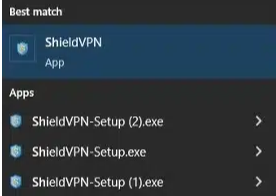
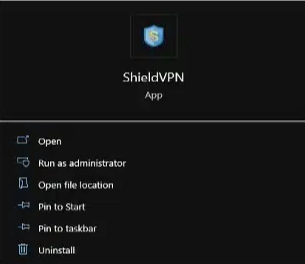
- If one of the VPN applications is found, an uninstaller is sometimes located under the Start menu option of the VPN application. The example image below shows an instance where the uninstall option isn't available.
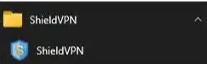
- If the application doesn't contain an uninstall option, then follow the steps below to attempt to uninstall the application:
- Click on the Start menu (Windows button) and type “Add or remove programs” to bring up the "Add or Remove Programs" menu.
- Search for the malicious software application names.
An example image below shows the ShieldVPN application found within the “Add or remove programs” application list. Once you find the application in the list, click on the application name and select the “Uninstall” option.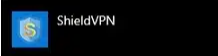
- After the application is uninstalled, you can try to verify that the application has been removed by clicking on "Start" (Windows Icon) and typing “File Explorer".
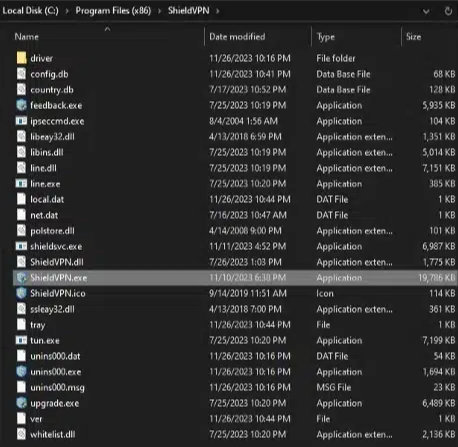
- Click on the drive letter “C:”—sometimes labeled as “Windows (C:)”—and navigate to "Program Files(x86)". Then, look for the malicious software application names in the list of files and folders.
- For ProxyGate, navigate to "C:\users\[Userprofile]\AppData\Roaming\ProxyGate".
- If you don't see any folder labeled "MaskVPN", "DewVPN", "ShineVPN", "ShieldVPN", "PaladinVPN" or "Proxygate" then this particular malicious software application may not be installed.
- If a service was found running, but not found under the Start menu or "Add or Remove Programs" then:
- Navigate to the directories described in directions 5d and 5e.
- Open “Task Manager".
- Select the service related to one of the identified malicious software applications running in the process tab.
- Select the option “End task” to attempt to stop the process from running.
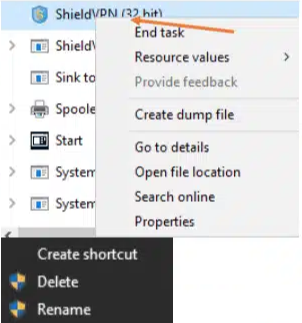
- Right-click on the folder named “MaskVPN”, “DewVPN”, “ShineVPN”, “ShieldVPN”, “PaladinVPN”, or "ProxyGate".
- Select the “Delete” option.
- You can also select all files found within the folder and then select the “Delete” option.
- If you try to delete the folder—or to delete all files located inside the folder—and receive an error message, be sure that you've ended all processes related to the malicious software within in Windows Task Manager, as described in step 5g.
- Click on the Start menu (Windows button) and type “Add or remove programs” to bring up the "Add or Remove Programs" menu.
保安建議
儘管「911 S5」已被海外執法機構搗破,但仍存在大量受感染裝置未被清除,需要持續監控。HKCERT已即時監測香港的「911 S5」感染情況,發現香港亦有裝置受感染,已將通知相關IP擁有者進行處理。HKCERT敦促公眾和機構對任何惡意軟件攻擊保持警惕,並採用下列防禦建議:
- 避免從未知或不可信來源下載VPN應用程式。
- 避免下載盜版或破解版軟件和遊戲。
- 定期檢查系統是否有異常活動或未知應用程式。
- 確保你的操作系統和應用程式已更新至最新的安全補丁。
- 安裝防病毒軟件,以檢測和防止惡意軟件感染。
- 定期監控網絡流量中的任何異常活動,以便及時發現潛在的安全漏洞。
- 制定明確的應變計劃以應對網絡安全事故。
參考資料
[2] https://thehackernews.com/2024/05/us-dismantles-worlds-largest-911-s5.html
[4] https://krebsonsecurity.com/2022/07/911-proxy-service-implodes-after-disclosing-breach/
分享至
