Massive "911 S5" Botnet Affecting Nearly 19 Million IP Addresses Worldwide was Dismantled
"911 S5" botnet impacted nearly 19 million IP addresses globally, posing a significant threat to cybersecurity. In May 2024, the FBI, in collaboration with international law enforcement agencies, successfully dismantled the "911 S5" botnet [1]. Although the "911 S5" botnet has been dismantled, its impact remains noteworthy. This article explores its operation and removal methods.

What is "911 S5"?
"911 S5" was a large-scale botnet primarily offering proxy services using IP addresses from infected devices. Cybercriminals could purchase these proxy services to make their online activities appear as if they originated from infected devices, thus concealing their digital footprints. They used these services to reroute their traffic through infected devices, hiding their true originating IP addresses and locations, and committing various crimes anonymously.
The botnet spread by distributing VPN applications with built-in malware targeting Windows systems. These VPN applications were often embedded in pirated games or software, enticing victims to download them. Once downloaded and installed, the VPN and malware would silently install on the victim's device, making it part of the 911 S5 botnet. VPN applications connected to the 911 S5 service included: MaskVPN, DewVPN, PaladinVPN, ProxyGate, ShieldVPN, and ShineVPN [1].
The Rise and Fall of the "911 S5" Botnet
The "911 S5" botnet emerged around 2014 and gradually grew to affect over 19 million IP addresses. It generated substantial revenue by providing proxy services to cybercriminals, facilitating malicious activities such as financial crimes, cyberattacks, and data theft [1][2][3].
In July 2022, a major security breach forced the botnet's administrators to take it offline [4]. However, by October 2023, it re-emerged under the name "CloudRouter". Despite this, international law enforcement efforts led to a significant breakthrough, resulting in the arrest of the botnet's administrators in May 2024, ultimately dismantling the "911 S5" botnet [1].
How to Remove "911 S5"
Even though the "911 S5" botnet has been dismantled, infected devices still pose a cybersecurity risk. It is crucial to immediately remove VPN applications associated with "911 S5". The FBI provides the following steps for users to check and remove the 911 S5 botnet from their devices [1]:
- Press Control+Alt+Delete on the keyboard and select the “Task Manager” option or right-click on the Start menu (Windows icon) and select the "Task Manager" option.

- Task Manager should now be running. Under the "Process" tab, look for the following:
- MaskVPN (mask_svc.exe)
- DewVPN (dew_svc.exe)
- PaladinVPN (pldsvc.exe)
- ProxyGate (proxygate.exe, cloud.exe)
- ShieldVPN (shieldsvc.exe)
- ShineVPN (shsvc.exe)
Example of running processes for ShieldVPN and ShieldVPN Svc:
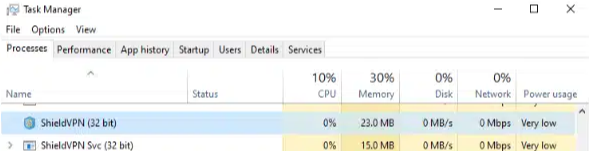
If Task Manager doesn't detect any of these services, verify that by searching the Start menu for any traces of software labeled as "MaskVPN", "DewVPN", "ShieldVPN", "PaladinVPN", "ProxyGate", or "ShineVPN".
- Click on the "Start" (Windows Icon) button typically found in the lower lefthand corner of the screen. Then, search for the following terms, which are the identified names of the malicious software applications:
- MaskVPN
- DewVPN
- ShieldVPN
- PaladinVPN
- ShineVPN
- ProxyGate
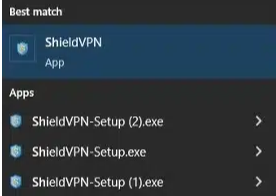
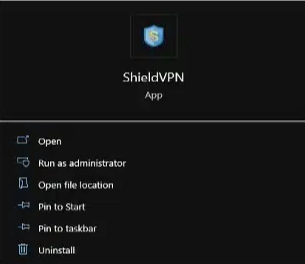
- If one of the VPN applications is found, an uninstaller is sometimes located under the Start menu option of the VPN application. The example image below shows an instance where the uninstall option isn't available.
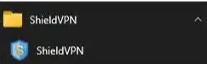
- If the application doesn't contain an uninstall option, then follow the steps below to attempt to uninstall the application:
- Click on the Start menu (Windows button) and type “Add or remove programs” to bring up the "Add or Remove Programs" menu.
- Search for the malicious software application names.
An example image below shows the ShieldVPN application found within the “Add or remove programs” application list. Once you find the application in the list, click on the application name and select the “Uninstall” option.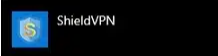
- After the application is uninstalled, you can try to verify that the application has been removed by clicking on "Start" (Windows Icon) and typing “File Explorer".
- Click on the drive letter “C:”—sometimes labeled as “Windows (C:)”—and navigate to "Program Files(x86)". Then, look for the malicious software application names in the list of files and folders.
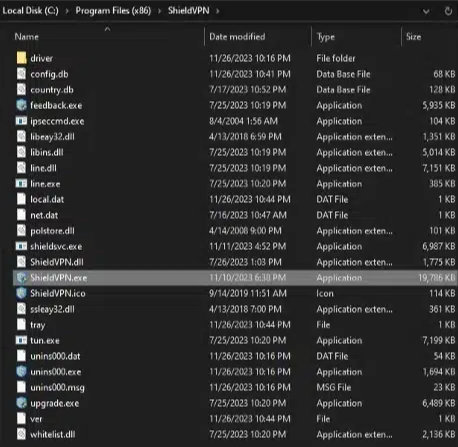
- For ProxyGate, navigate to "C:\users\[Userprofile]\AppData\Roaming\ProxyGate".
- If you don't see any folder labeled "MaskVPN", "DewVPN", "ShineVPN", "ShieldVPN", "PaladinVPN", or "Proxygate", then this particular malicious software application may not be installed.
- If a service was found running, but not found under the Start menu or "Add or Remove Programs", then:
- Navigate to the directories described in directions 5d and 5e.
- Open “Task Manager".
- Select the service related to one of the identified malicious software applications running in the process tab.
- Select the option “End task” to attempt to stop the process from running.
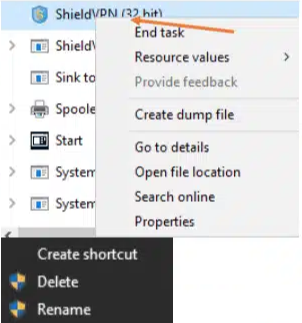
- Right-click on the folder named “MaskVPN”, “DewVPN”, “ShineVPN”, “ShieldVPN”, “PaladinVPN” or "ProxyGate".
- Select the “Delete” option.
- You can also select all files found within the folder and then select the “Delete” option.
- If you try to delete the folder—or to delete all files located inside the folder—and receive an error message, be sure that you've ended all processes related to the malicious software within in Windows Task Manager, as described in step 5g.
- Click on the Start menu (Windows button) and type “Add or remove programs” to bring up the "Add or Remove Programs" menu.
Security Advice
Although "911 S5" has been taken down by law enforcement overseas, infected devices may still exist and need continuous monitoring. HKCERT has also promptly monitoring 911 S5 infection in Hong Kong and found that some devices in Hong Kong are also infected. The relevant IP owners have been notified for action. HKCERT urges both individuals and organisations to stay vigilant and pay extra attention to any malware attacks, and adopt the following preventive measures:
- Avoid downloading VPN applications from unknown or untrusted sources.
- Avoid downloading pirated or cracked software and games.
- Regularly check your system for unusual activity or unknown applications.
- Ensure your operating system and applications are updated with the latest security patches.
- Install antivirus software to detect and prevent malware infections.
- Regularly monitor network traffic for any unusual activity to promptly indicate potential security breaches.
- Develop a clear incident response plan for responding to cybersecurity incidents.
Reference Links:
[2] https://thehackernews.com/2024/05/us-dismantles-worlds-largest-911-s5.html
[4] https://krebsonsecurity.com/2022/07/911-proxy-service-implodes-after-disclosing-breach/
Share with
