OpenSSL Multiple Vulnerabilities
Last Update Date:
2 Mar 2016 14:22
Release Date:
2 Mar 2016
4431
Views
RISK: High Risk
TYPE: Servers - Web Servers

Multiple vulnerabilities were discovered in OpenSSL. A remote user can decrypt TLS sessions in certain cases. Other vulnerabilities could cause denial of service on the target system.
TLS sessions could be decrypted by using a server supporting SSLv2. This cross-protocol attack is known as DROWN Attack (CVE-2016-0800). Systems are also affected if they share the same certificate used in a server running SSLv2 protocol.
Impact
- Denial of Service
- Information Disclosure
System / Technologies affected
- Versions prior to 1.0.1s and 1.0.2g
Solutions
- Upgrade to 1.0.1s or 1.0.2g
- Server operators should also disable the SSLv2 protocol.
- An online checking tool is available for examining the DROWN attack vulnerability. Users simply enters a domain or IP and it will tell you whether the server is vulnerable:
https://drownattack.com/#check
Not Vulnerable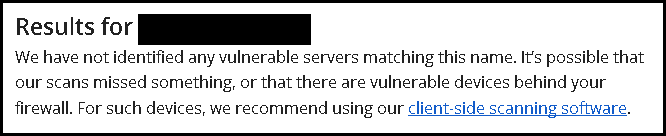
Vulnerable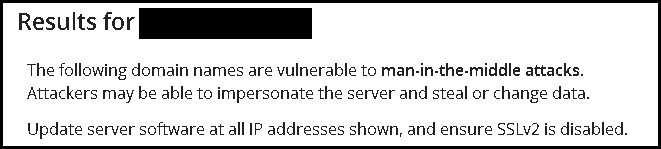
Vulnerability Identifier
- CVE-2016-0702
- CVE-2016-0703
- CVE-2016-0704
- CVE-2016-0705
- CVE-2016-0797
- CVE-2016-0798
- CVE-2016-0799
- CVE-2016-0800
Source
Related Link
Share with
