Analysing AgentTesla Spyware
According to Israeli cyber security solution provider Check Point’s “Global Threat Impact Index” monthly report published in early November[1], it was reported that AgentTesla continued to be one of the “Most Wanted Malwares” in the world, affecting over 7% of enterprises.
In this regard, HKCERT collected one of the samples of AgentTesla to analyse its attack vector and operations. Security advice is included at the end of the article to help the public protect against the threat.

What is AgentTesla? AgentTesla [2] is a spyware developed using .Net framework and designed for stealing user credentials. It first appeared in 2014. Hackers use this malware to spy on victims, intercept all user inputs in programs and browsers, and then transmit the information stolen to the Command-and-Control Server. |
Investigate the Malicious Email Attachment
Hackers usually send phishing emails to lure victims to download and execute the malware. In the collected sample, hackers used an email attachment named "PRE SHIPPING NOTICE.zip" to try to guide victims to download and open it.
We downloaded and opened the “PRE SHIPPING NOTICE.zip” file, a file named “PRE SHIPPING NOTICE.exe” was extracted.

Figure 1: A file named “PRE SHIPPING NOTICE.exe” is obtained after unzipping “PRE SHIPPING NOTICE.zip”
To check on VirusTotal website, a SHA256 hash value of the file is required. We executed the PowerShell cmdlet Get-FileHash to get the hash value of “PRE SHIPPING NOTICE.exe” and uploaded it to the VirusTotal.
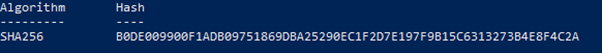
Figure 2: The SHA256 hash result
In the VirusTotal search result, 51 cyber security companies can identify the file as malware and AgentTesla.

#Search conducted on 24 November 2022
Figure 3: VirusTotal result
Analysing “PRE SHIPPING NOTICE.exe”
It is determined the file “PRE SHIPPING NOTICE.exe” is an executable file developed by VB.NET. Also, it is noted that no software packing technique is applied to the file.
What is Software Packing? Software packing is a method of compressing or encrypting an executable. Packing an executable will change the file signature in an attempt to avoid signature-based detection.[3] |

Figure 4: PRE SHIPPING NOTICE.exe is developed by VB.Net
Once we determined the programming language used, we used reverse engineering technique to get the code of “PRE SHIPPING NOTICE.exe”. A part of the code of “PRE SHIPPING NOTICE.exe” has shown that AgentTesla is using Windows ntdll.dll to inject the payload.

Figure 5: A part of the code after reverse engineering on “PRE SHIPPING NOTICE.exe”
After the payload had been executed, the behaviour detection of AgentTesla on the victim computer showed that it will steal the computer setting, credentials of system and browsers.

Figure 6: Use Code Access Security Policy Tool (CasPol.exe) to get the system sensitive information
Further deep dive into the stolen data using YARA malware research and detection tool found that it included mail profile setting (e.g. thunderbird, incredimail, MS Outlook), remote server credentials (e.g. WinSCP, FileZilla) and the login password stored in browsers (e.g. Firefox, Chrome)

Figure 7: Use Yara rules to scan out which files will be read by the sample
AgentTesla would transfer the stolen data via Telegram API to the hacker’s Telegram account.

Figure 8: Connection to the hacker Telegram account for data transfer
Security Advice
Malicious email is one of the spreading channels of AgentTesla. Moreover, different variants of AgentTesla have already appeared on the Internet. Hence, HKCERT recommends users to:
- Always keep the system, software, and antivirus software up to date
- Do not open unknown files, web pages and emails
- Confirm the legitimacy of sender and the content of the email before opening the attachments and links in the email,
- Check the file extension to avoid being misled by the file name. Do not open any executable file or Microsoft Office files with macros obtained from unknown source
- Executable file extension: .exe, .vbs, .js, .bat, msi, .ps, psc1, .cmd, .wsf, .jar, .reg, etc.
- Microsoft Office files with macros can be contained in all kinds of Office files (e.g. .doc/.docm, .xls/.xlsm, .ppt/.pptm). Users are advised to disable all macros from auto-run in the security settings[4].
- Use password management tools to manage the passwords instead of storing them on browsers
- Use lower privileged accounts for daily use instead of system administrator accounts
- Set up "multi-factor authentication" (MFA) to enhance the account security
Appendix
C&C IP Address:
Domain | IP Address |
api[.]telegram[.]org | 149.154.167.220 |
IOC:
Indicators | Indicator Type | File name |
B0DE009900F1ADB09751869DBA25290EC1F2D7E197F9B15C6313273B4E8F4C2A
| SHA256 | PRE SHIPPING NOTICE.exe |
Reference:
[2] What is Agent Tesla malware?
[3] Obfuscated Files or Information: Software Packing
[4] Enable or disable macros in Microsoft 365 files - Microsoft Support
Related Tags
Share with

