Malware Defense Guideline
Introduction
Today, one of the biggest threats that users and organization facing on the Internet is Malware. Malware is a general terminology and some common types of malware are viruses, worms, Trojan horse, botnets, spyware and adware. Malware can steals confidential information, damage system data and software on the computer and disrupt or disable the computer system and network. This article provides an overview and guidelines for defending your computer against malware.
This guideline is structured in the following sections. If you are familiar with the sections for understanding malware, you can refer to the protection guideline directly.
Understanding malware
- Why do hackers make malware?
- How malware gets into your computer?
- What techniques are used to maximize the spread of malware?
Protection guideline for malware
- How to protect yourself against malware?
Why do hackers make malware?
There are several reasons for hackers to make malware. Obviously, the primary objective is to make money from the victims and some of those reasons are more ridiculous than you expect. The followings are the targets that hackers want to achieve via malware.
Obtaining Personal Information
- To steal your personal information such as username and password of web sites, addresses, personal identification number, credit card number, email addresses, etc for financial benefit.
Controlling your computer to perform specific tasks
- To intrude into systems and implant malware, then further propagate and expand their access to other clean systems.
- To gain control and unauthorized use of compromised computers for illicit activities.
- To perform system intrusion or to cause loss of productivity through system slowdown or launching Distributed Denial-of-Service (DDoS) attack.
- To host phishing websites or to send spam email.
- To use your computer to attack other computers or systems in order to hidden their trail.
Gaining Personal Satisfaction
- To prove their technical skill and ability
- To be famous among other hackers in the black hat circle
- To revenge against hostile parties
How malware gets into your computer?
Malware are spreading rapidly by infecting user’s and organization’s computer systems. They are designed to take advantage on the vulnerabilities of operating systems and application programs. If the security patch of the system or security tool such as antivirus, is not installed on the system or not kept up-to-date, malware can be silently downloaded and installed on the system without user action. Below are the most common channels that malware can get into your computer systems.
Shared storage devices / USB flash drives
Shared storage devices and USB flash drives such as music player, video player, digital cameras and mobile phone are often used to share data among computers. Malware can easily be spreaded from infected computer to attached devices. When you attached these devices to your computer you might get your computer infected.
Peer-to-Peer file sharing program
Peer-to-Peer file sharing program allows people to download and share music, video, document file and any other file types freely and these files may be embedded malware, such as Document Malware.
Social Networking sites
By luring people to click on the user’s profile of other people, URL link or advertising banner on the social networking sites such as, Facebook, Twitter and MySpace etc. the malware will be downloaded and installed on your computer silently.
Rogue Security Software
These rogue software pretends to be legitimate system security programs to trick user to install it. Some malicious applications include fake browsers plug-ins, fake video/audio codec packs or free “online malware scanner”.
Web Browsing
A computer might be infected with malware merely by browsing a compromised web site. Please refer to “drive-by downloading” below.
Email or Instant Messaging (IM)
Hacker would send you an email or instant message with an attractive subject (i.e. Business Proposal or Big Sales) and a URL link or an attachment inside. This URL link and attachment will redirect you to a malicious web site and install malware on your computer.
What techniques are used to maximize the spread of malware?
Below are some techniques that hacker will be used to maximize the attack process in an unnoticeable manner and bypass security protection from antivirus tools.
Social Engineering
Social Engineering is a non-technical approach to trick the victim to disclose sensitive information or to take certain action. Typical examples of social engineering are spoofing the identity email sender or web sites (phishing) to gain trust, and using interesting subject or popular news so that people are more likely to open an infected attachment or clicking a deceptive URL link.
Blackhat Search Engine Optimisation (SEO)
It is a technique that manipulates relevance ranking to make infected links appear higher than legitimate results in search engine.
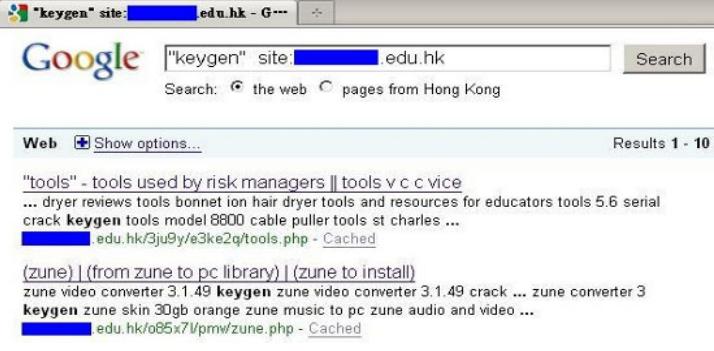
- Hackers have compromised a number of sites with malicious scripts that create web pages filled with the top search words or phrases.
- Malicious scripts fetch contents from third-party sites and include them in junk pages alongside the relevant search words or phrases so that the automatically generated webpage containing legitimate-looking content.
- As a user searches for related words or phrases, the infected links that rank high in the top of search result will generate a higher click rate to malicious websites.
- Users are likely to be redirected to bogus websites that come from poisoned search engine results and browser sends request to the malicious webpage which runs the attacker’s script.
Attackers’ script checks the request’s referrer field and if it contains specific sources, the script causes the browser to be redirected to another site that is serving malware or rogue security software.
The above modified “.htaccess” file in the compromised website is used to conditionally redirect search engine referred pages (of Google, AOL, MSN, …) to the malicious site “badsite.com.”
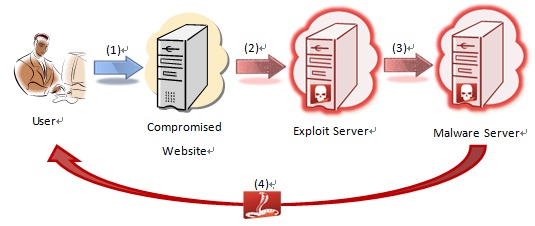
Drive-by download
It is the sequence of getting malware downloaded and installed after browsing an infected website or clicking a deceptive link in a vulnerable system.
- A user with a vulnerable system or browser visits a compromised website. The web pages of the compromised website were previously injected with invisible iframe or malicious script.
- Browser loads the embedded malicious iframe or script and is secretly redirected to another malicious exploit server.
- The exploit server detects the operating system and browser of the visitor and exploits the relevant vulnerabilities. If the visitor’s system and browser are not patched, they are exploited and caused execution of commands (called shellcode) that came with the exploit. The commands would cause the browser to connect to malware hosting URLs to download malware.
- Browser executes malware and then victim’s computer gets infected.
Clickjacking
It is a malicious technique to hijack user clicks on a web page to execute unsolicted code, resulting in data leakage of computer being taken control.
On a crafted clickjacked page, there is a set of dummy buttons or links which load another page over it in a transparent layer.
The users think that they are clicking the visible button or link, while they are actually performing actions on the hidden (transparent) page above it.
Clicking the dummy “Like” button will actually click the website menu on the hidden iframe.
The hidden page may be an authentic page and therefore the attackers can trick users into performing actions which the users never intended.
This may hide malware and other threats under the content of legitimate site. The hijacking clicks may further route users to other malicious page controlled by hackers.
How to protect yourself against malware?
If you do not want to be the next victim from malware, you should take cautious measures to build up your defenses and protect your computing devices against malware.
Protect your information
- Regularly change the password and keep it securely.
- Do not use the same password for different systems.
- Do not disclose any personal and financial information on the Internet
- Avoid performing any online transactions while using public workstations or public WiFi networks.
- Backup your important files and store it in a safe place.
Use security software
- Use antivirus and anti-spyware programs to prevent your computers from malware attacks. You can refer to HKCERT website (https://www.hkcert.org/security-tools) for the list of security defense tools.
- Always keep security program and related security signatures up-to-date.
- Schedule scanning the systems periodically.
- Install personal firewall. Personal firewall puts a protective barrier between your computer and the Internet and acts as a security guard to control access with other computers. It can detect and block the malicious network traffic between your computers and Internet.
Update your operating system and software regularly
- Enable auto update of the operating system and software. It can mitigates the risk of your computer from being compromised via exploits of know vulnerabilities.
- Disable the AutoRun feature on the CD/DVD Rom drive and USB storage devices. (Please refer to this URL: http://support.microsoft.com/kb/967715. Note also that Windows 7 does not display the AutoRun task in the AutoPlay dialog for devices that are not removable optical media (CD/DVD) to protect from malware infection.)
Practise safe web browsing
- Only download software from websites you trust. Be cautious of suspicious offer of free music, videos, games or cracked application which notorious for including malware in the download.
- Check before open attachments or click any link in email, instant message or social network website even if you know the sender.
- Do not click or download anything from an unexpected pop-up windows or warnings from a program that you did not install or do not recognize. Normally this software claims to protect your computer and able to remove spyware or viruses to tempt you to install.
- Turn on the security features such as phishing and malware protection on the web browser and avoid clicking any suspicious links.
Employ corporate standard practices (for SME)
- Classify data according to sensitivity. Define policy to handle data of different sensitivity levels including segmentation of data into different zones or networks, access control, data backup, contingency plan and incident response.
- Define procedures and guidelines for the usage of computer in corporate environment.
- Deploy security control system with features to protect against the attack from malware.
- Proactively monitor any violation or abnormal activities in order to identify and respond to potentially malicious network activities or unauthorized outbound connection attempts.
- Provide security awareness training to employee and encourage them to attend public seminar to improve their information security awareness.
You can refer to HKCERT (www.hkcert.org) or InfoSec (www.infosec.gov.hk) web sites for more details of “Security Guideline” and “Protecting your business”.
Share with




