Adobe Monthly Security Update (Nov 2017)
Last Update Date:
15 Nov 2017 09:49
Release Date:
15 Nov 2017
4479
Views
RISK: Medium Risk
TYPE: Clients - Audio & Video

Adobe has released monthly security update for their products:
| Vulnerable Product | Severity | Impacts | Notes | Details (including CVE) |
| Adobe Flash Player |  Moderately Critical Moderately Critical | Remote Code Execution | APSB17-33 | |
| Photoshop CC |  Moderately Critical Moderately Critical | Remote Code Execution | APSB17-34 | |
| Adobe Connect |  Moderately Critical Moderately Critical | Security Restriction Bypass Information Disclosure | APSB17-35 | |
| Acrobat and Reader |  Moderately Critical Moderately Critical | Remote Code Execution Information Disclosure Denial of Service | APSB17-36 | |
| InDesign CC |  Moderately Critical Moderately Critical | Remote Code Execution | APSB17-38 | |
| Digital Editions |  Moderately Critical Moderately Critical | Information Disclosure | APSB17-39 | |
| Shockwave Player |  Moderately Critical Moderately Critical | Remote Code Execution | APSB17-40 | |
| Adobe Experience Manager |  Moderately Critical Moderately Critical | Information Disclosure | APSB17-41 | |
| DNG Converter | 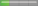 Less Critical Less Critical | Data Manipulation | APSB17-37 |
Number of 'Extremely Critical' product(s): 0
Number of 'Highly Critical' product(s): 0
Number of 'Moderately Critical' product(s): 8
Evaluation of overall 'Criticality Level': Moderately Critical
Impact
- Denial of Service
- Remote Code Execution
- Security Restriction Bypass
- Information Disclosure
- Data Manipulation
System / Technologies affected
- Flash Player 27.0.0.183 and earlier versions
- Photoshop CC 18.1.1 (2017.1.1) and earlier versions
- Adobe Connect 9.6.2 and earlier
- Adobe Acrobat and Reader 11.0.22 and earlier versions, 2015.006.30355 and earlier versions, 2017.011.30066 and earlier versions, 2017.012.20098 and earlier versions
- Adobe DNG Converter 9.12.1 and earlier versions
- InDesign 12.1.0 and earlier versions
- Adobe Digital Editions 4.5.6 and earlier versions
- Shockwave Player 12.2.9.199 and earlier
- Adobe Experience Manager 6.0 - 6.3
Please refer to the link below for detail:
http://blogs.adobe.com/psirt/?p=1510
Solutions
Before installation of the software, please visit the software manufacturer web-site for more details.
- The vendor has issued security updates for the products. Please refer to 'Details' column in the above table for details of individual product update or run software update
Vulnerability Identifier
Source
Related Link
Share with
