Next-Level Phishing: The Evolving Threat Landscape

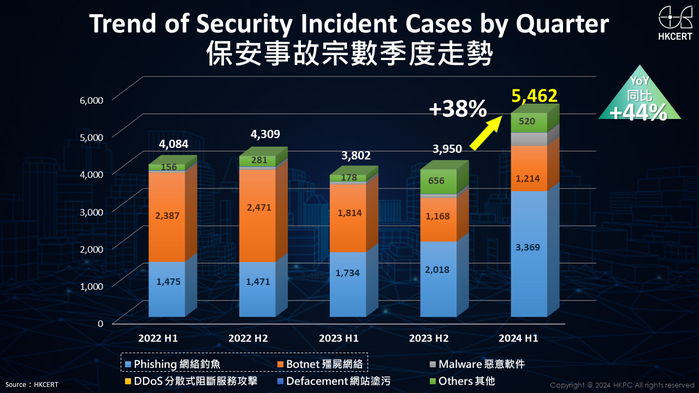
Phishing have become a common means of cybercrimes, but as technology advances, the methods used by criminals continue to evolve. As of the first half of 2024, HKCERT handled a total of 5,462 cybersecurity incidents, of which phishing accounted for 3,369 cases, contributing to more than half of the total cases. Compared to the second half of 2023, there was a staggering increase of 67%, highlighting the alarming nature of the situation.
Phishing, due to its low technical barrier, has become a prevalent form of cybercrime and a common starting point for many malicious campaigns. A simple email containing a phishing link has now evolved into a multifaceted and sophisticated threat, making it difficult to prevent.
HKCERT has also observed changes in phishing attacks. For example, criminals now use random combinations of numbers and letters to register phishing links to bypass domain detection and then employ URL shortening to make the links harder to identify at a glance. They also use cloud platforms to host phishing websites, thereby extending the removal time of these sites. To evade analysis, phishing websites may display phishing content based on the type of browsing device or operating system. For instance, if a desktop computer connects to the phishing site, it may be redirected to an official website. Conversely, if a mobile device is used to connect, it is directed to the phishing site. This significantly increases the complexity of analysis and detection.
This article will explore the techniques of next-level phishing and preventive measures.
Techniques of Next-Generation Phishing Attacks
Advanced Phishing Emails
Cybersecurity professional revealed that around 90% of cyber attacks originate from an email, including phishing emails. Traditional phishing emails often impersonate legitimate parties by using similar domain names, trademarks, and design styles, making the emails appear authentic and credible.
These emails typically use urgent or enticing language to prompt victims to immediately click on phishing links or malicious attachments. To prevent these emails from reaching users' inboxes, companies and email service providers employ filtering techniques to intercept emails containing phishing links or malicious attachments.
However, if phishing links are directly embedded in the email content, they are easily intercepted as the links can be readily filtered and checked. Conversely, hiding or loading links in other ways significantly increases the survival rate of phishing emails.
Phishing emails have evolved, for example embedding phishing links in QR codes (Quishing) and then sending them via email. He also noted that embedding the QR code in PDF or JPG files or encrypting files containing malicious QR codes can enhance the survival chances of phishing emails.
While there are solutions to scan QR codes in emails, a study revealed that hackers have started altering the background color and error ratio of QR code images in phishing emails, making it harder for email security measures to detect these QR codes.
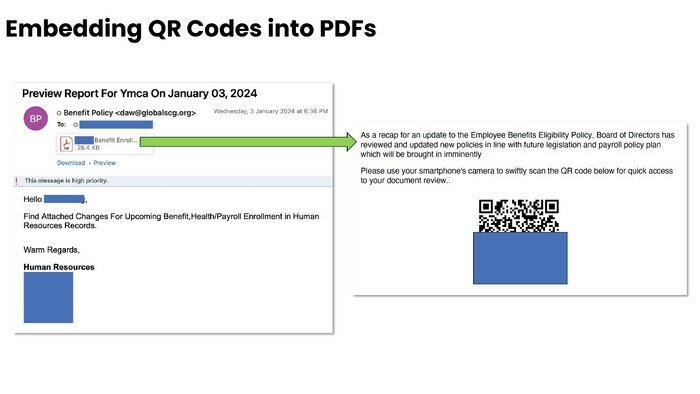


Images:Images are provided by Green Radar Limited
Another email-related phishing method called Clone Phishing. Hackers replicate a legitimate email with attachments and then resend it, impersonating the original sender but replacing the links or attachments with phishing links or malicious software.
Many Hopping
Attackers now often avoid sending direct phishing links. Instead, they send links that redirect users to their instant messaging channels, guiding users to join their channels for a conversation. Since these links are legitimate, they can bypass all cybersecurity measures. Once in the channel, attackers will send malicious links to lure users into clicking them.
Deepfake Scams
With the rapid development of artificial intelligence, deepfake is becoming more accessible. Some online platforms now allow users to experience deepfake technology, reducing the need for high computational power and training materials.
According to a research from Egress, Email Security Risk 2024, 63% of cybersecurity personnel surveyed were worried about the cyber attacks introduced by deepfake. To combat the attacks, there are also deepfake detection tools available on the internet, many of which are developed by major cybersecurity providers. A study has pointed out that synthetic images generated by artificial intelligence (AI) leave unique traces that are invisible to the human eye. By detecting these traces, it is possible to determine whether an image was generated by AI. The study also noted that the traces vary depending on the AI model, making it difficult for detection tools to be effective across all models.
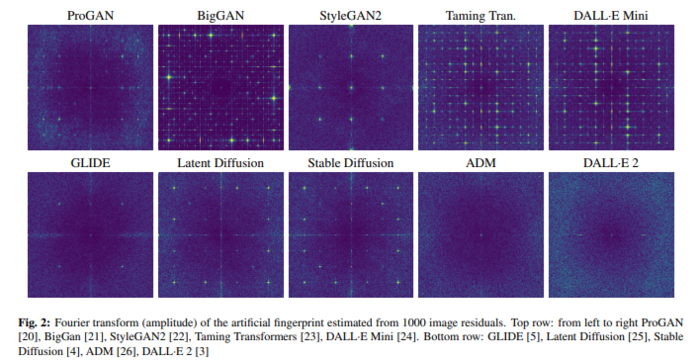
Deepfake technology also troubles social platforms, as it can generate realistic audio and video content, hindering our ability to judge online information. Currently, social platforms like Meta, Douyin and Xiaohongshu are using AI to tag AI-generated content to alert users.
HKCERT has published several articles analysing the security risks of deepfake, discussing the technology, real-life cases, and preventive recommendations. For more details, refer to the articles " Weaponisation of AI: The New Frontier in Cybersecurity", " Deepfake: Where Images Don't Always Speak Truth", and " Adopt Good Cyber Security Practices to Make AI Your Friends not Foes".
Phishing Adopting Search Engine Marketing (SEM)
The original intent of Search Engine Marketing (SEM) is to improve a website's search result ranking for relevant queries by paying for advertisements on search engines. This often results in these websites appearing higher than the results from organic searches. For example, when performing a search on Google, advertisements (websites marked as sponsored) appear first, followed by organic search results. Unfortunately, cybercriminals also exploit SEM to improve the search result rankings of phishing websites.
In 2023, the web version of the instant messaging platform, WhatsApp, was impersonated and successfully ranked at the top of search results using SEM techniques. When people searched for terms like "WhatsApp Web", fake websites were at the top of search results, leading to numerous WhatsApp accounts hijacked in Hong Kong.
In January 2024, a well-known pizza restaurant's website was similarly spoofed, resulting in credit card theft for some customers.
Photo:Sing Tao Daily
Phishing on Social Media
HKCERT has also observed phishing attacks extending to social media platforms, with fake company pages impersonating legitimate businesses. For example, in 2023, a travel agency's Facebook page was repeatedly impersonated. In the article " Taking Security Best Practice During Festive Season", HKCERT highlighted several characteristics of fake pages:
- The pixels of the company logo or image are low : Most of the images used by hackers are obtained by screenshots or stolen from other websites, and they are not the original images, so the pixels are lower. In addition, citizens could use Google Images to search if similar photo was found on other websites.
- Contact information is not detailed : The contact information displayed is not detailed, and the provided contact information is personal email or phone.
- The location of the management personnel is overseas : Citizens can check the location of relevant management personnel through this path "About" > "Page transparency" on the page. If the location of some management personnel is different from the location of the page, it is necessary to be vigilant about the authenticity of the page.
- Whether the page name is frequently changed and the establishment time : Fake pages often change their names and are established for a short period of time because their fraud methods are different each time.
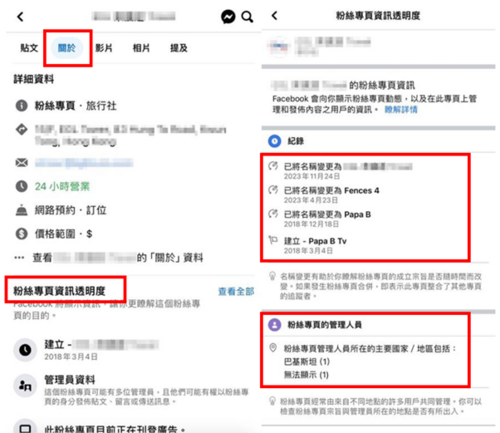
Photo Caption 1: Citizens can check the location of management personnel and establishment time through this path "About" > "Page transparency" on the page
- The page only has a small number of posts : Most of the posts on fake pages are copied from the past one to two months.
- Abnormal amount of likes/comments : Pay attention to whether the likes/comments come from countries outside the target group and whether the content of the comments is roughly the same.
Impersonating Customer Service
Recently, the number of "Impersonating Customer Service" scams on WeChat has surged dramatically. Scammers impersonate WeChat to send SMS messages claiming that the insurance you previously purchased has expired and that if you do not cancel, you will be automatically charged. The SMS includes a link to a fake customer service website or a fake telephone number, prompting you to contact the “customer service”.
Technique (Example)
- Receiving the SMS: The message mentions automatic charges, causing panic.
- Clicking the Link: You enter a fake website, which instructs you to contact online customer service.
- Making a Call: Clicking the link automatically dials a number to contact the fake customer service.
- Increasing Credibility: The fake customer service will guide you to open a so-called "official authorization letter" within the WeChat app.
- Extracting Information: The fake customer service uses the excuse of canceling the renewal to induce you to provide your bank or credit card details and passwords.
- Stealing Funds: Scammers use the obtained information to transfer money from your account or misuse your credit card.
WeChat "Impersonating Customer Service" scams are constantly evolving, giving rise to different fraudulent methods. Some scams even use WhatsApp, WeChat instant messaging, or cold calls to carry out similar frauds. Citizens need to stay vigilant and keep up with the latest scam tactics.
In addition to fake WeChat customer service, scammers have also been found impersonating Microsoft and Apple technical support. These scammers set up phishing websites. And then abuse the one of the Google Tools to mimic various Google products, and use search engine advertising to place these sites at the top of search results. When users search for "google {product}" (e.g., google Translate) in a search engine, these malicious sites appear among the top results.
When users click on these links, they are taken to a page that appears to be google.com, but in reality, it is just an image of the google.com page loaded with malicious links. If the user clicks on the image, a window will pop up indicating that there is an issue with the computer and instructing the user to contact Microsoft or Apple technical support. The screen will then enter full-screen mode. Once the user contacts the fake technical support, the scam begins.
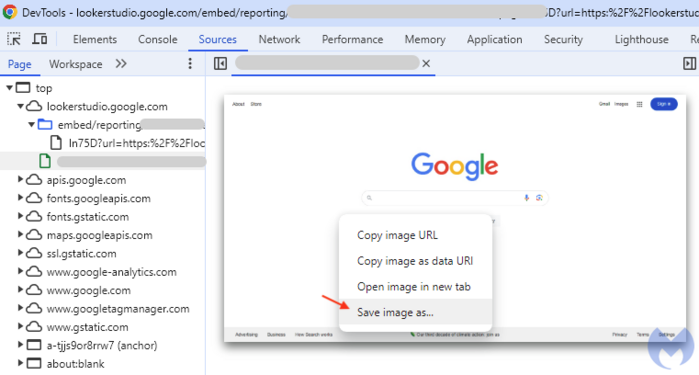
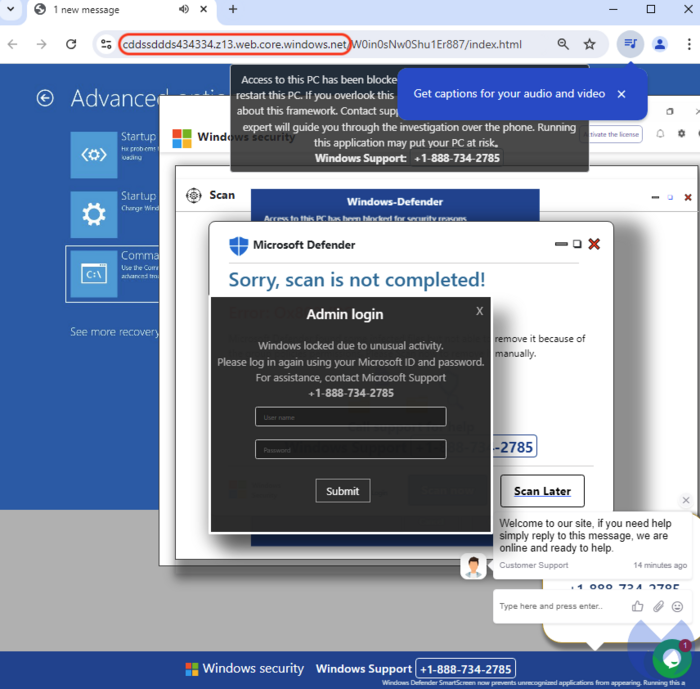
Photo:Malwarebytes
Protect Against Phishing
Employee Education and Training
Regular employee education and training are the primary measures to prevent phishing. Companies should organise phishing drills to help employees learn how to spot phishing messages through practical exercises. HKCERT provides numerous training materials on the website and has a thematic page on phishing, teaching citizens how to recognize and prevent it. For more details, refer to the "All-Out Anti-Phishing" page.
Multi-Factor Authentication (MFA)
Implementing multi-factor authentication can significantly increase the difficulty for attackers to gain control of accounts. Even if passwords are compromised, additional authentication steps are required to log in.
Email Filtering
Equipping email filtering systems to filter out suspicious phishing messages can intercept them before they reach the recipient's inbox.
Establish a Comprehensive Incident Response Plan
Organisations should develop detailed incident response plans to quickly mitigate damage when a phishing attack is detected. This includes regular data backups, ensuring clear communication channels, and defining the roles and responsibilities of each department. HKCERT has also created a security incident response guide for businesses, outlining the tasks to be performed before, during and after security incidents. For more details, refer to the "Incident Response Guideline for SMEs".
Regular Security Audits
Conduct regular security audits to identify and patch potential security vulnerabilities. The audit process should include simulated phishing attacks to test the effectiveness of existing defences.
Install Antivirus Software
Install security software to safeguard against phishing attacks. At the same time, use the free search engine “Scameter” of Cyberdefender.hk to identify frauds and online pitfalls through email, URL or IP address, etc.
Conclusion
Next-level phishing poses serious threats to individuals and businesses. By understanding the characteristics and techniques of these attacks and implementing effective countermeasures, we can reduce the risks and losses they bring. Continuous vigilance, comprehensive employee education and robust cybersecurity measures are key to combating next-level phishing.
Reference
- https://www.greenradar.com/green-radar%e5%85%ac%e4%bd%88%e5%b9%b4%e5%ba%a6%e9%9b%bb%e5%ad%90%e9%83%b5%e4%bb%b6%e5%a8%81%e8%84%85%e6%8c%87%e6%95%b8-%e6%8f%ad%e9%9c%b2%e9%bb%91%e5%ae%a2%e8%a1%8c%e9%a8%99%e6%96%b0%e6%8b%9b/
- https://www.egress.com/media/o1sbpq5t/egress_email_security_risk_report_2024.pdf
- https://arxiv.org/pdf/2211.00680v1" target="_blank
- https://www.chinadaily.com.cn/a/202408/16/WS66c2c173a31060630b923cad.html
- https://about.fb.com/news/2024/04/metas-approach-to-labeling-ai-generated-content-and-manipulated-media/
- https://cyberdefender.hk/en-us/
- https://www.malwarebytes.com/blog/scams/2024/08/dozens-of-google-products-targeted-by-scammers-via-malicious-search-ads
Share with
