Security News
Phishing Scams: How To Recognize A Scam Email, VOIP call, or Text

Zombinder on Dark Web Lets Hackers Add Malware to Legit Apps

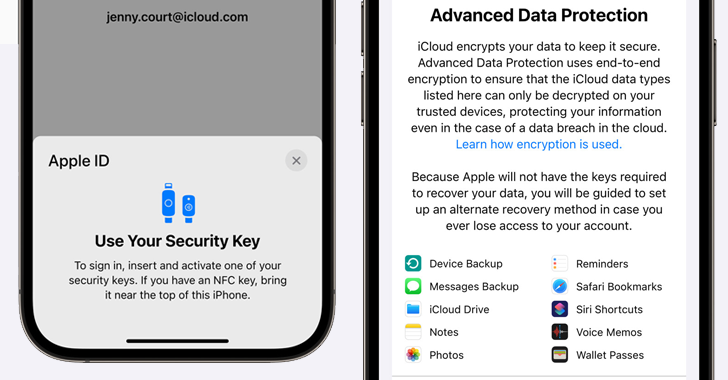
Apple Boosts Security With New iMessage, Apple ID, and iCloud Protections
New Google Chrome feature frees memory to make browsing smoother

Apple rolls out end-to-end encryption for iCloud backups

How to locate a user's GPG key in Thunderbird

Rackspace Incident Highlights How Disruptive Attacks on Cloud Providers Can Be

Microsoft: Hackers target cryptocurrency firms over Telegram

Hackers use new, fake crypto app to breach networks, steal cryptocurrency
Rackspace rocked by ‘security incident’ that has taken out hosted Exchange services

