Fight Ransomware
FIGHT
Ran$omware
齊抗勒索軟件
What is Ransomware?
Ransomware is a type of malware threat actors used to encrypt all the files of the victim and hold data as hostage. During the initial infection, the ransomware will try to spread through the victim's network, including servers, accessible computers, connected external devices or shared drives, and other accessible systems, making the files, databases, or applications inaccessible until the attacker provides the decryption key for data recovery. The attacker would then demand a ransom payment in exchange for the decryption key for data recovery.
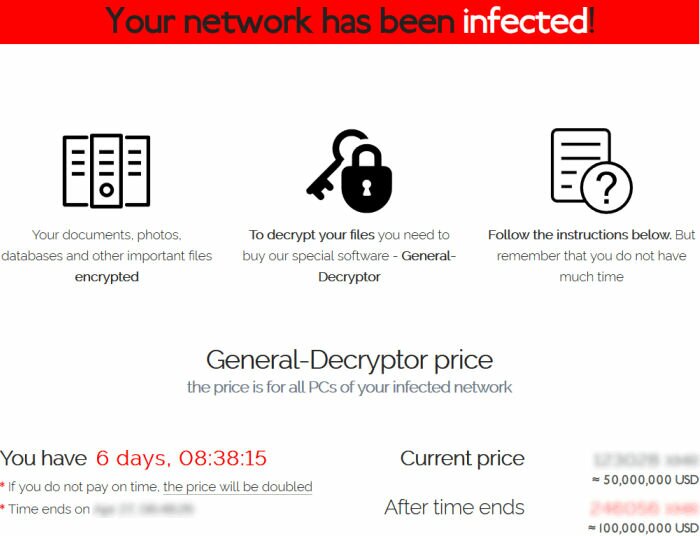
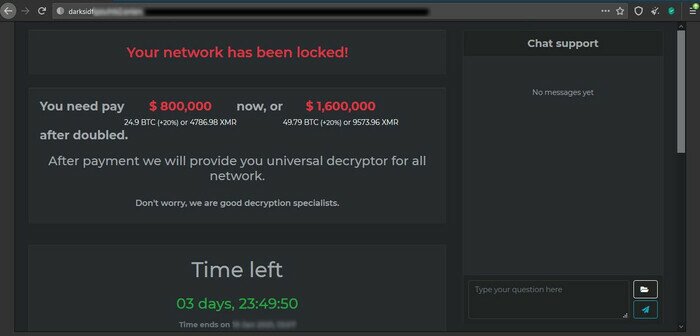
(Figures above) REvil and DarkSide ransomware gangs demanding ransom payment.
Human-operated ransomware
Unlike traditional ransomware attacks, like WannaCry, spreading across the Internet automatically, human-operated ransomware is “hands-on-keyboard” persistent attacks controlled by a group of skilled hackers with plenty of IT knowledge infiltrating the networks of the organisations. They use their skills to circumvent different security controls or exploit software vulnerabilities, and remain persistent in the network for further malicious actions. As such, it has become one of the biggest cyber threats for organisations nowadays. While encryption is the major means in the attacks, hackers can also use other malicious tactics according to the situation, such as steal credentials, or access and exfiltrate data from compromised systems to maximise the impact of the attacks. The whole attack chain consists of system infiltration, data exfiltration, encryption, threat of data disclosure or even disruption of the critical infrastructure system, negotiation and putting pressure on victim. Some ransomware hackers have already turned the attack into a business operation with multiple extortion methods and cooperated with other hacker groups to share the ransom payments. Some well-known human-operated ransomware attacks are REvil, Conti, Lockbit and Ryuk.
Ransomware as a Service (RaaS)
Ransomware as a Service (RaaS) is one of the business models adopted by hackers. Its operation is similar to that of the Software as a Service (SaaS), in which software developers lease their SaaS products. In RaaS, ransomware operators offer infrastructure or services required to perform a ransomware attack, negotiation and ransom collection services, and then sell them as a package to other hacker groups. The relevant hacker groups do not require the necessary skills to develop or use the ransomware, and can focus on targeting the victims, such as carrying out the network penetration or spreading phishing emails. As such, both sides can leverage their abilities and earn substantial dividends from the ransom payments. This ransomware model brings benefits to both parties and is one of the reasons why ransomware attacks continue to grow worldwide.
Consequences and impact
Ransomware attacks can cause severe direct and indirect consequences and impacts including:
Consequences
- Data exfiltration
- Data encryption
- Backup destruction
- Disruption to systems and operations
Impacts
- Paralyse business operation
- Damage an organisation’s reputation
- Suffer significant financial loss for business recovery
- Drop of stock prices
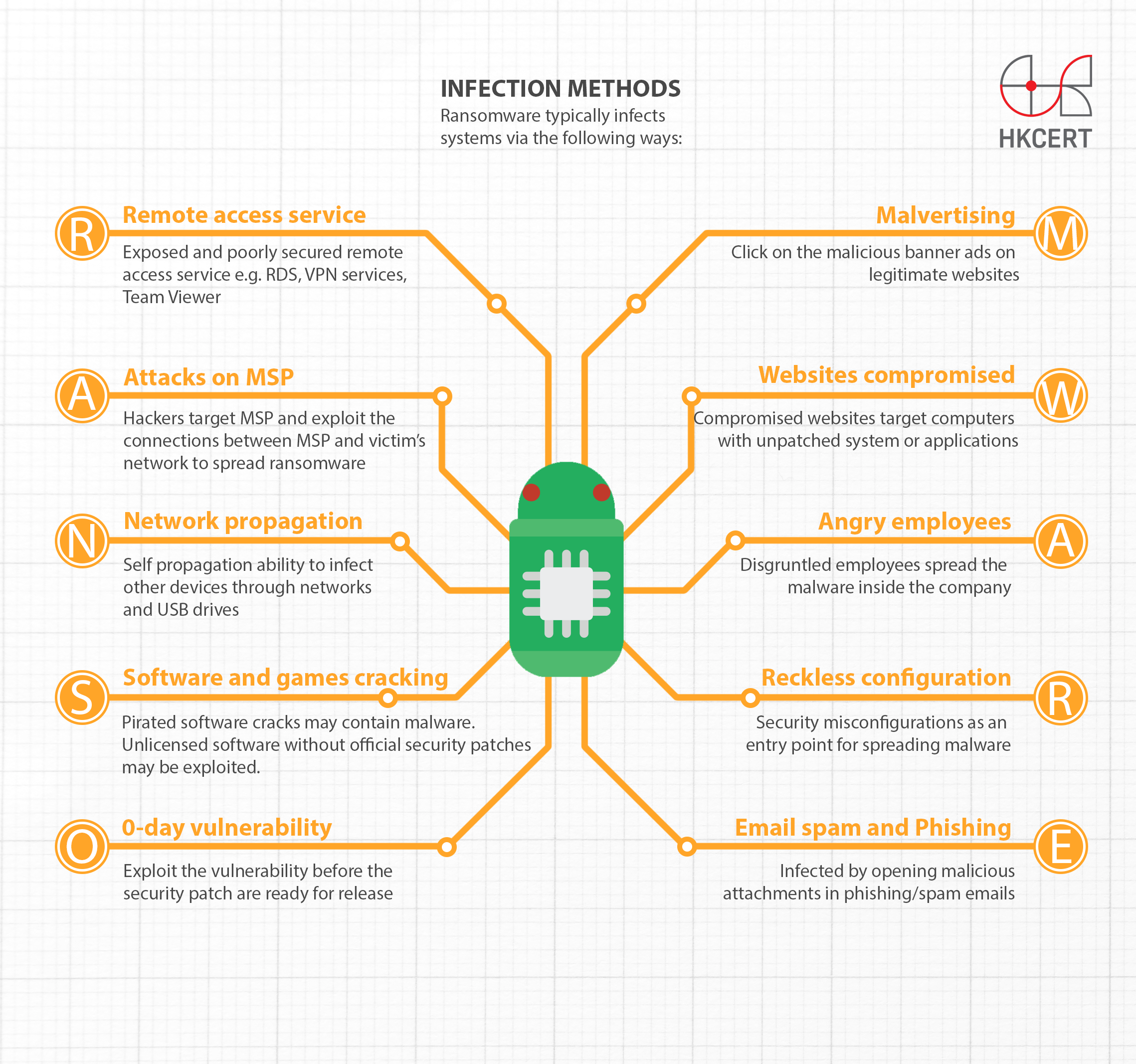
Infection Methods
Ransomware typically infects systems via the following ways – RANS0MWARE:
1. Remote access service
Hackers often launch attack (e.g. password brute force attack) on exposed and poorly secured remote access service, e.g. RDS, VPN services, TeamViewer, etc to penetrate into the insecure systems and spread ransomware.
2. Attacks on managed service providers (MSP)
Hackers may target the managed service providers of the victim. Once gained access to the network of the MSP, they can exploit the trusted connections between the MSP and the victim’s network to spread the ransomware.
3. Network-propagation
While most ransomwares are Trojan that do not spread by itself, some have evolved to have propagation ability. Once a ransomware infects a computer, it will try to infect other devices through networks and USB drives etc.
4. Software and games cracking
Pirated software and games not only illegal but also a source of malware and ransomware infections. Some hackers plant ransomware into software cracks to attract user to download and install. Also unlicensed software usually is unable to perform security update. It creates a loophole for attacker to exploit the vulnerabilities.
5. 0-day vulnerability
Hackers may exploit the software vulnerability before the security patch are ready for release or yet to deployed by the users.
6. Malvertising
Malvertising is the short form of malicious advertising. Some victims were infected by visiting legitimate websites with malicious banner ads.
7. Websites that are compromised
Some victims were infected by visiting compromised websites. Those websites target computers with unpatched system or applications, including browsers and plugins.
8. Angry employees
Hackers may directly contact the disgruntled employees to spread the ransomware inside the company network and return a certain percentage of ransom paid by the company to the person.
9. Reckless configuration
Security misconfigurations allow hackers to abuse as an entry point to the organization for spreading ransomware.
10. Email spam and Phishing
Majority of victims were infected by opening malicious attachments in phishing or spam emails. Known file types of malicious attachments include compressed file (.zip) containing executable files (.exe) or JavaScript files (.js), and macro enabled Microsoft office files (.doc, .xls). The phishing email campaign was usually generated by attacker-controlled botnets infrastructure.
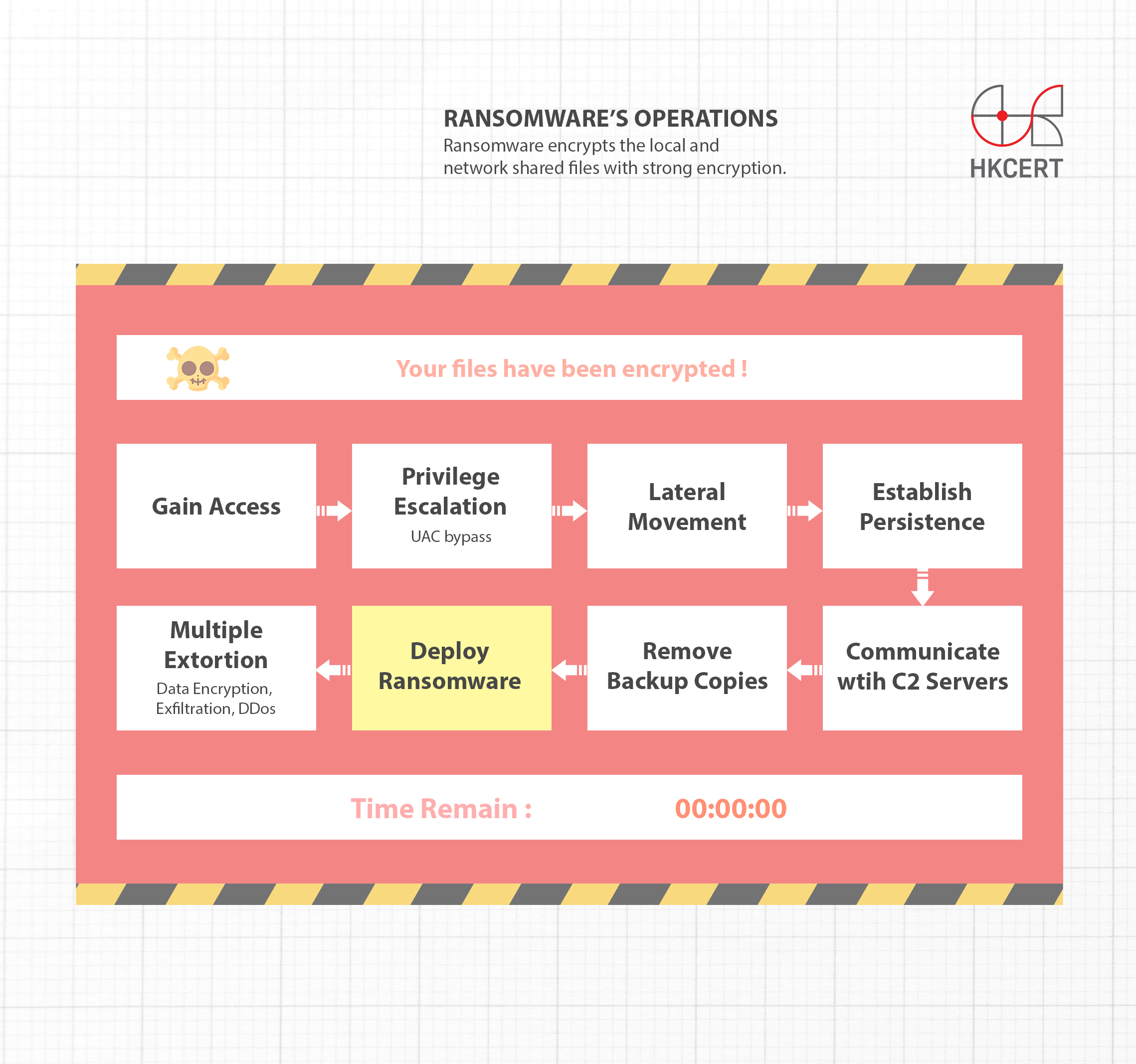
Ransomware's Operation
Ransomware encrypts the local and network shared files with strong encryption. Targeted file types include documents, images, videos, editable drawing files, database files, digital certificates, game profiles, etc.
After the encryption, the ransomware will send the encryption key back to the control and command server (C2 server) and leaves an extortion message on the infected computer. It demands a specified amount of ransom in bitcoins to exchange for the decryption key before a certain due date, otherwise, the hackers threaten to delete that unique decryption key.
In the past, if the victims have performed regular offline backup, they can restore backup data to resume operation, effectively safeguarding critical data against ransomware and avoiding the extortion attempt. As this single-extortion tactic became ineffective, a new tactic was introduced - double extortion. The hackers would first scan the network and learn the system architecture of the victim once gained unauthorised access. They will then look for important information such as financial data, business secret, personal data, etc. and extract a large quantity of these information before encrypting them. Once succeeded, they will threaten to release or sell the stolen information, exerting greater pressure on the victims to pay the ransom.
In the latest development, hackers have resorted to applying different extortion methods to heighten the pressure and threat on victims for a greater amount of ransom payment. These methods include launching distributed denial-of-service (DDoS), contacting victims’ customers, short selling victims’ stock, affecting infrastructure systems, etc. As this tactic involves more than two extortion methods, it is called multiple extortions.
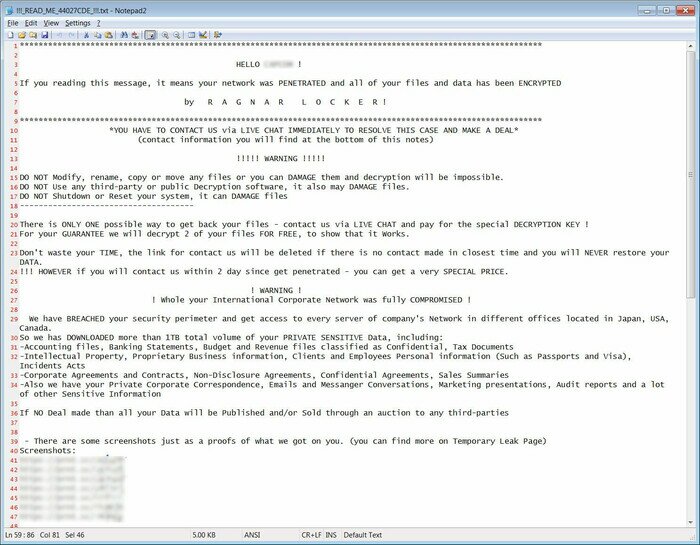
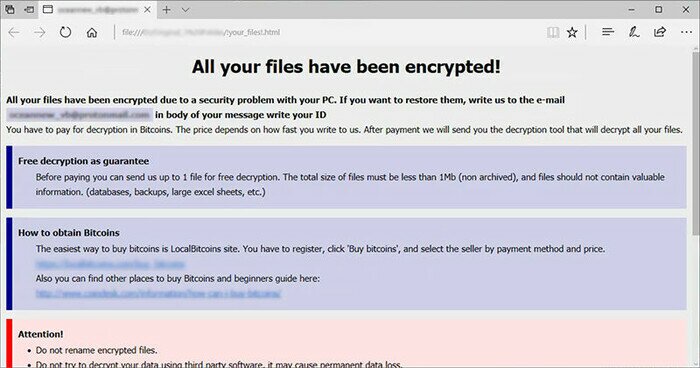
(Figures above) Ragnar and GlobeImposter ransom notes demanding a ransom payment
Incident handling
If you are infected by ransomware:
DON'T ✘
- Don't pay the ransom as it merely sponsors hackers’ operation;
- Don't use unauthenticated decryption software which searchable online, you may be infected with other malwares at your own risk;
- Don't open any file before removing the ransomware; and
- Don't restore the system if no backup was done previously to avoid losing information required for decryptions.
DO ✔

- Isolate and disconnect the infected system from network (LAN and WiFi) and remove any external storage such as USB hard disk immediately to avoid further infection and impacts;
- Follow the general decryption steps:
- Search for the decryption tool in the webpage: https://www.nomoreransom.org/en/decryption-tools.html;
- Copy the encrypted files to an empty storage device;
- Use a clean computer and tool(s) above to decrypt the files;
- The steps of using the decryption tool(s) can refer to the user manual of the tool.
- Download legitimate cleanup tool, and run a full scan to remove the ransomware;
- Restore the files and data from the backup, if backup files are available;
- Employ Intrusion Detection Tool to find the loopholes and understand the cause of the attack. Perform a comprehensive security scan and reinforce the security protection in time.
- Report the incident to HKCERT
Useful Guidelines
Ransomware Decryption Guideline
Help: How to handle ransomware infection
Prevention
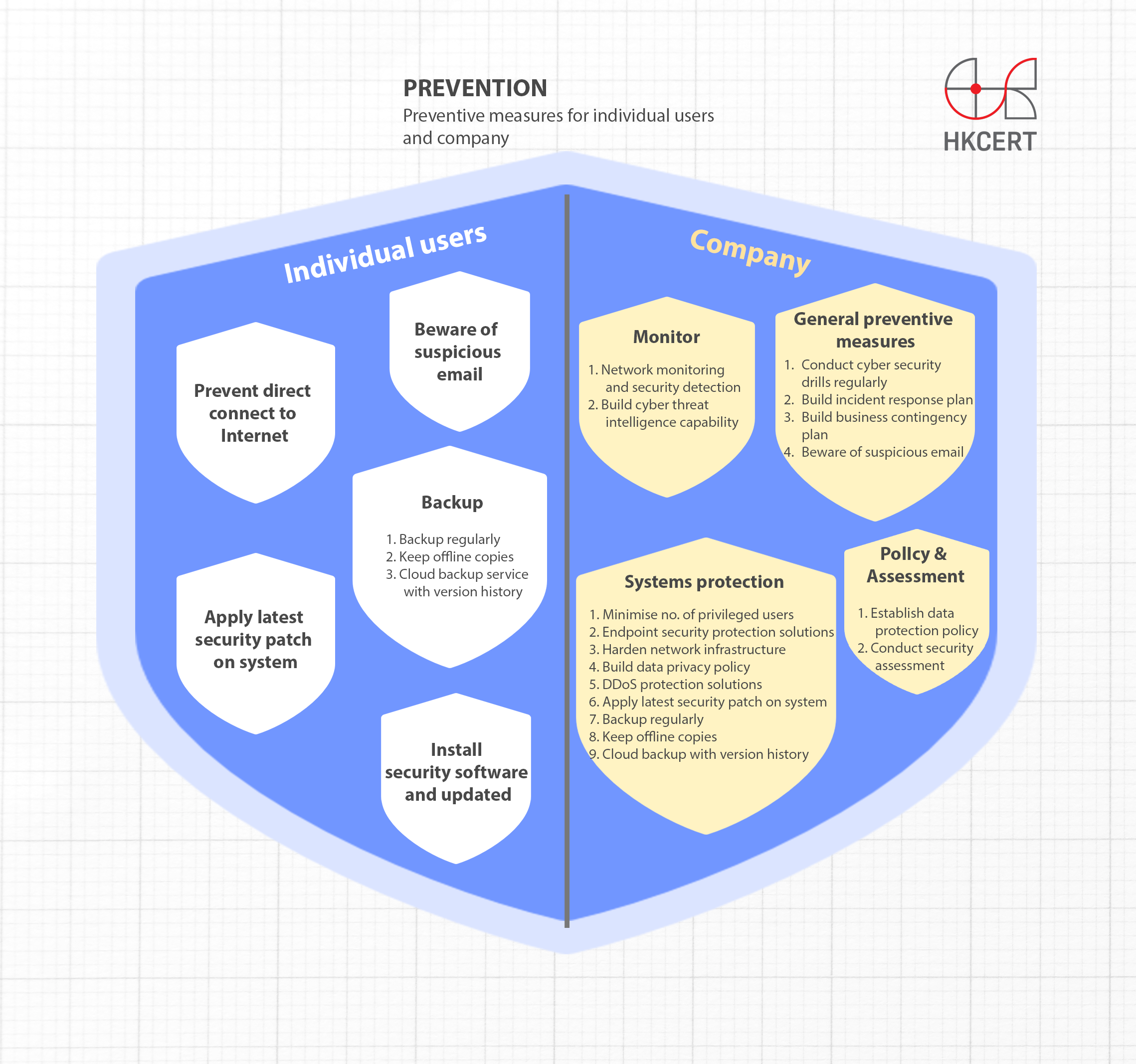
For individual users
- Beware of suspicious email. Do not click on the link or open the attachment, especially compressed files (zip), executable files (exe), macro-enabled document files and program script (vbs, js, ps, bat)
- Always update the system and software with the latest security patch
- Ensure the instalment of security software such as anti-virus or Internet security application, and have its signature updated regularly
- Prevent your devices from connecting to the Internet directly, e.g. set up a router or even firewall to filter malicious network traffic
- Backup the important documents instantly and regularly. Keep an offline copy of the backup to avoid being affected by the malware.
- If you are using cloud backup service, make sure that the cloud service provider has a version history function. It can help to recover the files from previous version, even though the affected files are synchronized to the cloud.
For company
- Policy and Assessment
- Establish a data protection policy to cover the complete information life cycle, from collection, processing data to destruction of data;
- Conduct security assessment regularly and plug loopholes found;
- Protect your systems
- Minimise the number of users with privileged access (e.g. domain administrative rights) to confine the scope and impacts in case of an attack, and use general account in day-to-day operation;
- Implement endpoint security protection solutions to inspect emails and web content for malicious payloads, detect and quarantine malicious programs to prevent malware infection, and have its signature updated.;
- Harden the network infrastructure and minimise the points of exposure to the Internet;
- Build data privacy policy which consists of sensitive data encryption and password policies and handling of encryption keys in isolation;
- Consider applying DDoS protection solutions or services to defend against DDoS attacks;
- Update the system and software with the latest security patch.
- Backup the important documents instantly and regularly. Keep an offline copy of the backup to avoid being affected by the malware.
- If you are using cloud backup service, make sure that the cloud service provider has a version history function. It can help to recover the files from previous version, even though the affected files are synchronized to the cloud.
- Monitor your systems and detect malicious activities
- Ensure network monitoring and security detection are in place and ready to carry out immediate incident response if any abnormal network activities are detected;
- Build cyber threat intelligence capability to keep track with most recent threats, and exchange information with peer organisations to pre-empt emerging attacks;
- General preventive measures
- Conduct cyber security drills regularly, such as phishing drills and ransomware attack drills, and training to improve employees’ security awareness;
- Build incident response plan to respond to ransomware, data leakage, DDoS attacks in a timely manner;
- Build business contingency plan to minimise the impact to business in case of ransomware, DDoS and OT systems outage incident;
- Beware of suspicious email. Do not click on the link or open the attachment, especially compressed files (zip), executable files (exe), macro-enabled document files and script (vbs, js, ps, bat)
Different Types of Ransomware
| Ransomware | Ransom Message | File Extensions | Primary Infection Vector | Decryptable Versions* |
| Akira | A file named "akira_readme.txt" asking victims to contact the hacker to pay ransom. | The extension is ".akira". |
| Akira |
| AstraLocker | A file named "How To Restore Your Files.txt" asking victims to contact the hacker to pay ransom. | The extension is ".Astra " and ".babyk". |
| AstraLocker |
| BianLian | A file named "Look at this instruction.txt" asking victims to contact the hacker to pay ransom. | The extension is ".bianlian". |
| BianLian |
| BlackByte | A file named "BlackByte_restoremyfiles.hta" asking victims to contact the hacker to pay ransom. | The extension is ".blackbyte". |
| BlackByte |
| Cactus | A file named "cAcTuS.readme.txt" asking victims to contact the hacker to pay ransom. | The extension is ".cts" followed by a digit. For example ".cts1". | exploited vulnerabilities of Fortinet VPN devices,
exploited vulnerabilities of Qlik Sense. | No descryption tool for Cactus |
| Cerber/Magniber | A message asks victims to buy 'Cerber/My Decryptor' for decryption via Tor browser. | V1-V3 is “.cerber”.
In Magniber, the common extentions are ".ypkwwmd", ".ndpyhss", ".wmfxdqz", ".axlgsbrms", ".nhsajfee", ".mqpdbn", ".damdzv", ".qmdjtc", ".mftzmxqo", ".demffue", ".dxjay", ".fbuvkngy", ".xhspythxn", ".dlenggrl", ".skvtb", “.vbdrj”, “.fprgbk”, ".ihsdj", ".mlwzuufcg" or ".kgpvwnr" |
| Cerber V1
Magniber: Some extensions are supported by the decryption tool.
|
| CrySIS/Dharma/Phobos | A file named "FILES ENCRYPTED.txt" or ransom notes with .HTA and .TXT extension in encrypted folder shows contact information of the hacker. The message asks victims to contact the hacker to pay ransom. | The common extensions are ".java", ".arena", ".bip" and ".phobos". |
| Some extensions are supported by the decryption tool. |
| DarkSide/BlackMatter | In DarkSide, ransom notes named "README.[victim's_ID].TXT", asking victims to pay ransom for decryption on a designated webpage via Tor browser.
In BlackMatter, ransom message is posted on a black screen wallpaper. Ransom notes named "[random_string].README.txt" asking victims to pay ransom for decryption on a designated webpage via Tor browser. | In DarkSide, the extension is victim's ID.
In BlackMatter, the extension is random. |
| DarkSide
No descryption tool for BlackMatter |
| Djvu | Files named "_openme.txt", " _open_.txt" or "_readme.txt" shows contact information of the hacker. The message asks victims to contact the hacker to pay ransom. | The common extensions are ".djvu", "djvu*", ".djvuu", ".udjvu", ".djvuq", ".uudjvu", ".djvus", ".djuvt", ".djvur" and ".DJVUT". |
| Some extensions are supported by the decryption tool. |
| eCh0raix | Ransom notes named "README_FOR_DECRYPT.txtt" or "README_FOR_DECRYPT.txt", asking victims to pay ransom for decryption on a designated webpage via Tor browser. | The commaon extension are ".encrypt" and ".encrypted". |
| No descryption tool for eCh0raix |
| ESXiArgs | Ransom notes named "ransom.html" or "How to Restore Your Files.html", asking victims to contact the hacker to pay ransom. | The commaon extension is ".args". |
| ESXiArgs-Recover |
| GandCrab | A message asks victims to pay ransom for decryption on a designated webpage via Tor browser. | In V1, the extension is ".GDCB". In V2 and V3, the extension is ".GRAB". In V4, the extension is ".KRAB". In V5, the extension is random |
| GandCrab V1, V4 and V5 up to V5.2 |
| GlobeImposter | A file named "HOW_TO_BACK_FILES.txt" or "how_to_back_files.html" in encrypted folder shows victim’s personal ID serial number and contact information of hacker. The message asks victims to send ID serial number to hacker's email address, then pay ransom according to hacker's instruction. | In 1.0 version, the common extension is ".CHAK". In 5.1 version, the common extension is ".IQ0005". |
| GlobeImposter 1.0 |
| Hades | A file named “README_RECOVER_FILES_[victim_id].html”, "README_RECOVER_FILES_[victim_id].png" or "README_RECOVER_FILES_[victim_id].txt" in each folder containing encrypted files, which shows victim’s personal identification ID, the link for purchasing the decryption password and hacker's email address. The message asks victims to hacker's provided link, then pay ransom according to hacker's instruction. | The common extension is ".MafiaWare666", ".jcrypt", ".brutusptCrypt", ".bmcrypt", ".cyberone", ".l33ch". |
| Hades |
| HermeticRansom | A file named “read_me.html” on the victim’s Desktop folder shows victim’s personal ID serial number and contact information of hacker. The message asks victims to send ID serial number to hacker's email address, then pay ransom according to hacker's instruction. | The common extension is ".[[email protected]] .encryptedJB". |
| HermeticRansom |
| Hive | A file named "HOW_TO_DECRYPT.txt" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The version 1 extension is ".hive" The version 2 extensions are ".w2tnk" and ".uj1ps" All random string extension of version 3 and 4 |
| Hive |
| LockBit | A file named "Restore-My-Files.txt" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The extension is ".abcd". |
| LockBit |
| LockerGoga | A file named "README-NOW.txt" or "README_LOCKED.txt" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The extension is ".locked". |
| LockerGoga |
| Maze | Ransom message is posted on a screen wallpape. A file named "DECRYPT-FILES.html", asking victims to contact the hacker and follow the hacker's intrution to pay ransom. | The extension is random. |
| No descryption tool for Maze |
| MegaCortex | Victims with data encrypted by versions 2 through 4 need the ransom note (e.g. “!!READ_ME!!!.TXT”, “!-!README!-!.RTF”, etc) present. | The extension is “.aes128ctr”. |
| MegaCortex |
| MortalKombat | It changes the desktop wallpaper to give it a Mortal Kombat theme and generates a ransom note called | The extension is “..Remember_you_got_only_24_hours_to_make_the_payment_if_you_dont_pay_prize_will_triple_Mortal_Kombat_Ransomware” | spreads through phishing emails and targets exposed RDP instances. | MortalKombat |
| Muhstik | A message asks victims to pay ransom for decryption on a designated webpage via Tor browser. | The extension is ".muhstik". |
| The device whose ID includes in below keys list can be decrypted. |
| Nemty | Nemty’s ransom message is [extension]-DECRYPT.txt. The message asks victims to pay ransom for decryption on a designated webpage via Tor browser. | In Nemty, the extension is ".nemty". |
| Some file types encrypted by specific versions of Nemty can be decrypted. |
| Netwalker | A file named "{ID} – Readme.txt" asking victims to pay ransom for decryption on a designated webpage via Tor browser. | The extension is random. |
| No descryption tool for Netwalker |
| Rhysida | A file named "CriticalBreachDetected.pdf" asking victims to pay ransom for decryption on a designated webpage via Tor browser. | In Rhysida, the extension is ".rhysida". |
| Rhysida |
| Ryuk/Conti | In Ryuk, files named "RyukReadMe.txt" or "RyukReadMe.html" shows contact information of the hacker. The message asks victims to contact the hacker to pay ransom.
In Conti, a file named "CONTI_README.txt" shows contact information of the hacker. The message asks victims to contact the hacker to pay ransom. | In Ryuk, the extension is ".RYK".
In Conti, the extension is ".CONTI", ".KREMLIN", ".RUSSIA", ".PUTIN". |
| No descryption tool for Ryuk and Conti
Some of the versions of Conti with extention ".KREMLIN", ".RUSSIA", ".PUTIN" can be decrypted. |
| SEXi | A file named "SEXi.txt" contain a message telling the victims to download the "Session" messenger app and to contact them at the listed address. | The extension is ".SEXi". |
| No descryption tool for SEXi |
| Sodinokibi/REvil | Ransom message is posted on a blue screen wallpaper. Ransom notes are placed in each folder with the message asking victims to pay ransom for decryption on a designated webpage via Tor browser. | The extension is random. |
| Sodinokibi/REvil decryption tool |
| STOP | A file named "_openme.txt" or "_readme.txt" in encrypted folder shows victim’s personal ID serial number and contact information of hacker. The message asks victims to send ID serial number to hacker's email address, then pay ransom according to hacker's instruction. | The common extensions are ".puma", ".pumas", ".coharos" and ". STOP". |
| Some extensions are supported by the decryption tool. |
| Trigona | Trigona’s ransom note is dropped to the system with the name how_to_decrypt.hta. The HTML code in this file contains embedded JavaScript functionality. | The extension is "._locked". | exploited software vulnerabilities | No descryption tool for Trigona |
| WannaCry | A file named "info.hta" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The extension is ".WannaCry". |
| WannaCry |
| Yanluowang | A file named "README.txt" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The extension is ".yanluowang". |
| Yanluowang |
| Yashma | A file named "Restore_Files.html" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The extension is ".AstraLocker" or 4 random alphanumeric-characters. |
| Yashma |
*You can identify ransomware and download decryption tools from the website below. HKCERT makes no guarantee of the tools for successful recovery of the files. *
https://www.nomoreransom.org/en/index.html
Blogs about ransomware
Resources
External Resources
- No More Ransomware
https://www.nomoreransom.org/en/index.html - CISA Stop Ransomware
https://www.cisa.gov/stopransomware - ACSC - Ransomware
https://www.cyber.gov.au/ransomware - BGD e-GOV CIRT - Ransomware Prevention & First Response Guideline
https://www.cirt.gov.bd/ransomware-guideline-2021-version-1-0/ - BtCIRT - Ransomware
https://www.btcirt.bt/ransomware/ - CERTNZ - How ransomware happens and how to stop it
https://www.cert.govt.nz/it-specialists/guides/how-ransomware-happens-and-how-to-stop-it/ - CNCERT/CC - 勒索软件防范指南
https://www.cert.org.cn/publish/main/8/2021/20210723084543714582413/20210723084543714582413_.html - CyberSecurity Malaysia - Crypto Ransomware
https://www.mycert.org.my/portal/details?menu=431fab9c-d24c-4a27-ba93-e92edafdefa5&id=116c71b6-c4d8-40fb-a3f3-3906e7db5e53 - KrCERT/CC - Ransomware Response Guide
https://www.boho.or.kr/krcert/publicationView.do?bulletin_writing_sequence=35410&queryString=cGFnZT0xJnNvcnRfY29kZT0mc29ydF9jb2RlX25hbWU9JnNlYXJjaF9zb3J0PXRpdGxlX25hbWUmc2VhcmNoX3dvcmQ9cmFuc29td2FyZQ== - mmCERT - STOP Ransomware Guide
https://www.mmcert.org.mm/media/8 - SingCERT - Protect Your Systems and Data From Ransomware Attacks
https://www.csa.gov.sg/singcert/Advisories/ad-2020-006 - TWCERT/CC - 勒索軟體防護專區
https://antiransom.tw/index.html
Past Events
Fight Ransomware Campaign - Ransomware Awareness Training
31/F, Great Eagle Centre, 23 Harbour Road,Wan Chai, Hong Kong
Cisco Systems (Hong Kong)
Seminar: Protecting Data from Ransomware Attacks Build a Secure Cyberspace 2016
Office of the Government Chief Information Officer (OGCIO)
Hong Kong Police Force (HKPF)
Hosting firm's VMware ESXi servers hit by new SEXi ransomware

LockBit ransomware returns to attacks with new encryptors, servers

Medusa Ransomware on the Rise: From Data Leaks to Multi-Extortion

New Black Basta decryptor exploits ransomware flaw to recover files

Black Basta ransomware made over $100 million from extortion