NTP Abused to Launch Distributed Reflection Denial of Service Attack (DRDoS)
RISK: High Risk
TYPE: Attacks - DDoS

Network Time Protocol (NTP) and other UDP-based protocols can be used to amplify denial-of-service attacks. Servers running the NTP based on implementations of ntpd prior to version 4.2.7p26 that use the default unrestricted query configuration are susceptible to a reflected denial-of-service (DRDoS) attack. Other proprietary NTP implementations may also be affected.
In NTP DRDoS attack, the attacker sends a spoofed packet with their source address being the IP of a victim. The NTP server replies to this request, but the size of the response sent is an amplified amount compared to the initial request, resulting in a denial-of-service on the victim. The two highest message types, REQ_MON_GETLIST and REQ_MON_GETLIST_1 amplify the original request by a factor of up to 3660 and 5500 respectively. This bandwidth amplification factor (BAF) is a bandwidth multiplier based on the number of UDP payload bytes that are sent by the server in comparison to the UDP payload bytes of the request. Other message types can also be used in this attack, but REQ_MON_GETLIST and REQ_MON_GETLIST_1 create the biggest impact.
An unauthenticated remote attacker may leverage the vulnerable NTP server to conduct a distributed reflection denial-of-service (DRDoS) attack on another user.
It was reported that the NTP was abused in the wild to launch DRDoS attack in Dec 2013.
For details about DRDoS, please refer to a blog article to be published by HKCERT.
Impact
- Denial of Service
System / Technologies affected
- ntpd versions prior to 4.2.7p26
Solutions
Before installation of the software, please visit the software manufacturer web-site for more details.
- If you can apply an update:
Update to ntpd versions 4.2.7p26 and later.
- If you cannot apply an update, or want to secure NTP after update, please consider the following recommendations:
- Disable REQ_MON_GETLIST and REQ_MON_GETLIST_1 by adding "disable monitor" in /etc/ntp.conf file. You can check whether they are disabled by running the following commands:
# ntpdc
> monlist
***Server reports data not found
- You can also check whether your NTP server (input XXX.XXX.XXX.XXX/32) is vulnerable for abuse in DRDoS, with the following website:
http://openntpproject.org/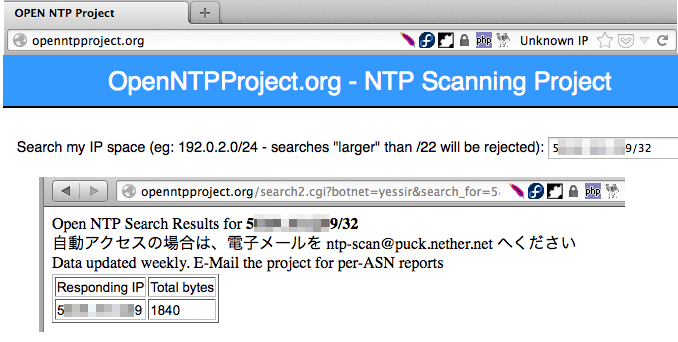
If similar result is returned, your NTP server is vulnerable.
- Disable REQ_MON_GETLIST and REQ_MON_GETLIST_1 by adding "disable monitor" in /etc/ntp.conf file. You can check whether they are disabled by running the following commands:
- Best practice
- Disable unused services or ports.
- If you need not run a public NTP server, set up your NTP installation to act as a client only.
- Implement secure NTP template:
http://www.team-cymru.org/ReadingRoom/Templates/secure-ntp-template.html
- Perform ingress filtering on your firewall, i.e. block any packets from outgoing if their source IP address is not within the network.
- Disable unused services or ports.
- Special note to ISP
- If you are an ISP, please assess your network configuration to ensure you do not allow spoofed traffic. Implementing BCP38 is highly recommended in order to perform ingress filtering.
- If you are interested to know more about the open NTP servers in your AS, you can use this URL: http://openntpproject.org/searchby-asn.cgi?search_asn=[AS number]
- If you are an ISP, please assess your network configuration to ensure you do not allow spoofed traffic. Implementing BCP38 is highly recommended in order to perform ingress filtering.
Vulnerability Identifier
Source
Related Link
Share with
