Botnet Detection and Cleanup

1. Introduction
Botnet is one of the major security threats nowadays. Smart devices such as computers, mobile phones, and IP cameras run the risk of being infected and becoming part of a botnet. Hackers can remote control them to participate in illegal activities, launching sophisticated and destructive attacks, which result in wider information leakages and severe service disruptions, causing massive losses.
HKCERT has been closely monitoring the development of botnets, taking different follow-up actions in response to attacks, and issuing timely security recommendations to users to fix vulnerabilities and raise awareness.
2. What is Botnet?
Literally, “Bot” is short for “robot”, and adding the “net” to it creates “botnet” which means “a network of bots”; and the hacker who controls other people's computers is called "bot herder".
Once a device is installed with a "bot software" via malware infection, “bot herder” can make the bot do anything by issuing commands via a command and control (C&C or C2) server. A botnet typically consists of hundreds or even millions of devices, including PC, Mac, Linux servers, home router, smartphone etc.
The combined resources of these controlled devices can be used to launch destructive or sophisticated attacks like sending billions of spam email, huge bandwidth DDoS and targeted financial fraud.
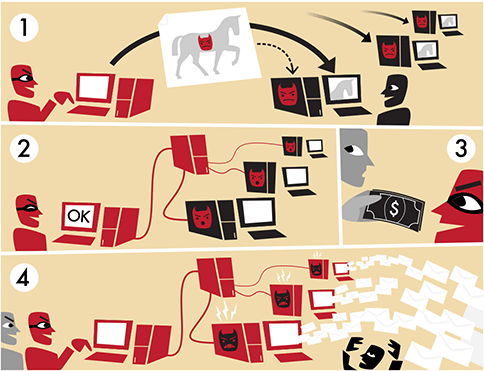
How botnet works (image created by Tom-b: http://commons.wikimedia.org/wiki/File:Botnet.svg)
3. General Cleanup Instructions
The following instructions are applicable to the cleanup of typical botnet infection on Windows PC. You can also refer to other cleanup tools on "Security Tools" page (click here). For specific botnet and solution on other platforms, please refer to the next section.
- Visit https://docs.microsoft.com/en-us/windows/security/threat-protection/intelligence/safety-scanner-download, and based on download either 32-bit or 64-bit version of “Microsoft Safety Scanner” in accordance with the version of Windows whom your computer is operating on.
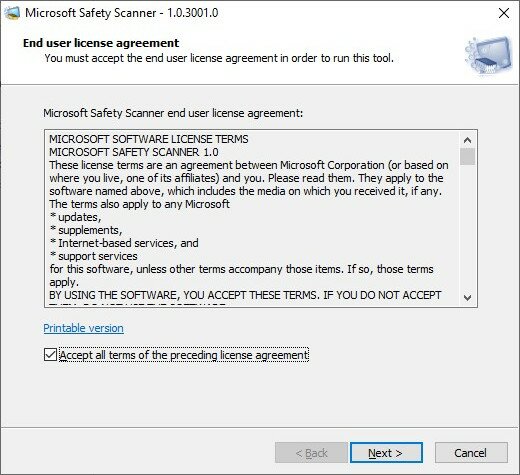
- Run msert.exe. Accept the license agreement by ticking the "Accept all terms of the preceding license agreement" check box and click “Next”.
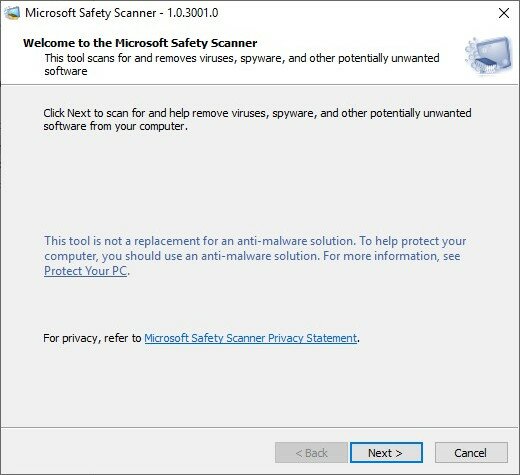
- Click “Next” to proceed with initial scanning.
- Select “Full scan” and click “Next” to start scanning.
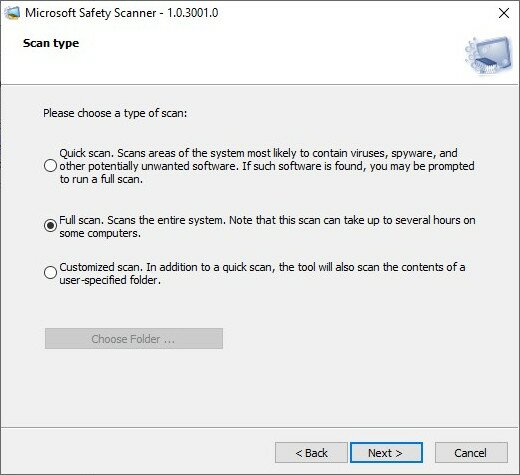
- Scanning is in progress which can last several hours, depending on the volume of files in the computer. Please ensure sufficient power for the device to prevent the interruption.
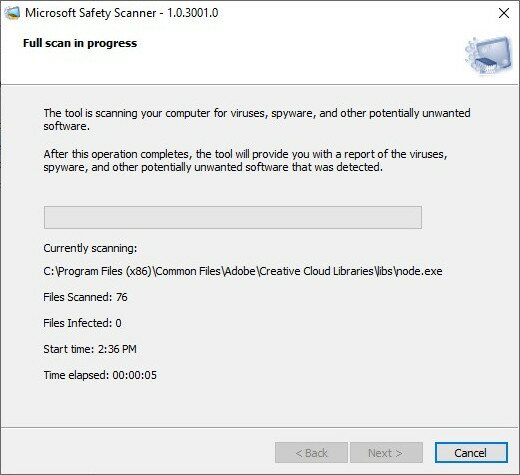
- If your computer is not infected with any malware, the result will show that “no viruses, spyware, and other potentially unwanted software were detected”.
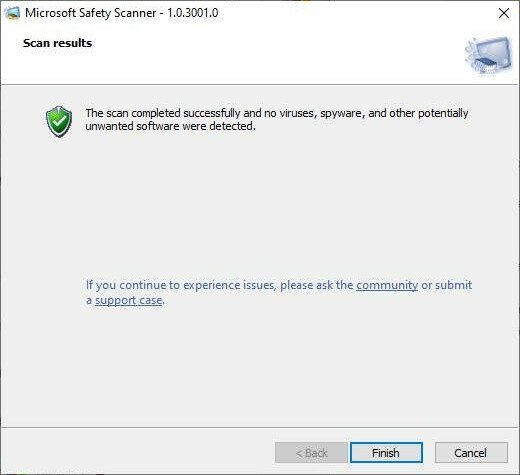
- If your computer is infected with some botnet malware, it will be detected and removed by the scanner.
4. Detection & Cleanup of Active Botnets in HK
| Botnet | 1st Operation | Detection and Cleanup Reference |
|---|---|---|
| 911 S5 | 2024-10 | Massive "911 S5" Botnet Affecting Nearly 19 Million IP Addresses Worldwide was Dismantled |
| Emotet | 2021-03 | Party’s over for Emotet, One of the World’s Most Feared Botnets |
| QSnatch | 2021-03 | QSnatch Malware Prevention and Cleanup |
| Vpnfilter | 2018-05 | Malware "VPNFilter" Affecting Networking Devices Worldwide |
| Necurs | 2018-05 | Please refer to Section “3. General Cleanup Instructions” shown above |
| Mirai | 2017-08 | Mirai Malware Cleanup and Prevention |
| Avalanche | 2016-02 | HK Victims Reported in Global Takedown of "Avalanche" Cybercrime Hosting Platform |
| Ramnit | 2015-06 | Ramnit Botnet Detection and Cleanup in Hong Kong |
| GameOver Zeus | 2014-06 | GameOver Zeus Botnet Detection and Cleanup in Hong Kong |
| ZeroAccess | 2013-08 | ZeroAccess Botnet Detection and Cleanup in Hong Kong |
| Pushdo | 2013-08 | Pushdo Botnet Detection and Cleanup in Hong Kong |
| Citadel | 2013-06 | How to detect and remove Citadel Malware |
Appendix A: Follow up actions on Botnet by HKCERT
In response to the development of botnet in Hong Kong, HKCERT has taken the following actions in recent years:
- Take down C2 server: Collaborate with law enforcement to help collect evidence and take down C2 servers located in Hong Kong.
- Gather bot information: Collaborate with security researchers, CERT teams, security vendors and software vendors to gather Hong Kong IP addresses detected with botnet connection. HKCERT also proactively collects such information via open source intelligence (OSINT) and its own Information Feed Analysis System (IFAS) on regular basis.
- Notify device owner: After consolidating the bot information, we will collaborate with ISPs to inform the owners of the devices on the IP addresses.
- Increase public awareness on botnet and clean up guidance: HKCERT publishs articles about botnets active in Hong Kong to raise public awareness and provides instructions on detecting and cleaning up bot malware infection.
